I went out for a lunch walk the other day to clear my head and listened to a really great episode of Freakonomics. The episode Honey I grew the economy focused on the process and motivators that drive innovation. The deep dive into drivers in particular resonated a lot with me. I saw parallels to how we approach IT as we kick off 2020. While that was super interesting, it wasn’t a giant leap for me to ask a similar question of:
Why do we get engaged in the various technological communities and what do we derive from those communities?
This seemed like a fun opportunity to hear from some of our Technology Community members to understand: Why do we vCommunity?
To Learn
For me, first and foremost, vCommunity is about Education. It stands to reason that it’s the most common entry point for people to engage. It makes sense: You need help on a topic, so you go looking around and only then do you learn about the plethora of opportunity’s available to you. When I personally started down the virtualization path, training dollars were tight, so to improve my knowledge I had to look elsewhere and as luck would have it, I found the Boston VMUG UserCon. That free one day training, gave me access to educational presentations, subject matter experts and hands on training. It was a formative moment for me, and opened my eyes to other avenues of learning. It also showed me that there were a ton of engaged people out there sharing via different mediums.
Stalwart of the vCommunity, Kyle Ruddy had something similar to share regarding his introduction to the tech communities “What I wasn’t ready for was the amount of blogs out there detailing issues I had run into. It was a complete lightbulb moment. From that point it was a gradual process of moving from reading blogs to creating blogs.”
Kyle also highlights a hallmark of the community in that there tends to be a strong desire to contribute back in the form of blogs, videos, podcasts and a host of other mediums. That was after all the genesis for VirtualVT as well. If you look at the mechanics of sharing content, it takes time and effort. You can’t help but boost your knowledge whenever you’re contributing technical content, because you end up spending more time with the underlying technology’s. Unintentional education? Knowledge Osmosis? Whatever you call it, the brain gets bigger the more you feed it, and you have to keep feeding if you’re creating content about technologies.
To Grow
Bolstering your knowledge via the educational opportunities the communities provide is definitely a path to bigger and better things, but I’ll let you in on a not-so-secret, secret. Getting involved and putting yourself out there as a contributing member of the community can be equally impactful on your career. Contributing is an idealistic endeavor, but it often has the side effect of building your brand at the same time. I met the MVP power couple of Dave and Cristal Kawula this past fall and in a recent blog post Dave shares a bit about how he and Cristal started MVPDays and the impact their event has had on a specific community member: “…I talked him into doing his first presentation, which led to him speaking at user groups and conferences. Earlier this year he became a Microsoft MVP, and a few days ago, he actually accepted a position at Microsoft.”
The experience that Dave highlights is not unique to MVPDays. It crosses groups and goes to the heart of what Matt Heldstab (VMUG Board of Directors) shared with me recently “The fantastic power of this vCommunity and its ability to elevate the careers of its members never ceases to amaze me.”
It’s Fun!
vDodgeBall, vSoccer, vPoker are just a few of the side-events that come to mind for ways that we like to enjoy the lighter side of our geekdom. One of my favorite events was when our 2017 vExpert party was held at the Pinball Museum in Las Vegas. The reality is that many of us work really hard and through a plethora of events, engagement in the vCommunity can be a nice way to blow off some steam. My friend AJ Murry who I co-led a local VMUG group with, hits on this point “In the vCommunity I have found my people. I have made life long friends. I have learned great things and shared amazing experiences.”
It’s all about the people
 I mean it’s referred to as the vCommunity for a reason! The one theme that comes up time and time again when talking about our tech communities, was the value of our peer connections. We learn, share and when times are tough, we support each other. Nikola Pejkova, Veeam Vanguard Community Mangager highlights the value of these connections: “I love being part of community because it enables its members cooperate together, strengthen and enrich their knowledge and learn from each others experiences.”
I mean it’s referred to as the vCommunity for a reason! The one theme that comes up time and time again when talking about our tech communities, was the value of our peer connections. We learn, share and when times are tough, we support each other. Nikola Pejkova, Veeam Vanguard Community Mangager highlights the value of these connections: “I love being part of community because it enables its members cooperate together, strengthen and enrich their knowledge and learn from each others experiences.”
Everywhere I’ve gone and nearly everyone I’ve interacted with has been gracious with their knowledge and time. It’s a hallmark of these communities and a reason why there are so many deep bonds. You see it in every independent blog post, every community presentation and every response to a forum post. That’s the real magic to the vCommunity: We want to be there for each other and to collective lift each other up!
So how do YOU get involved?
It’s an amazing thing being part of this community, but like many things in this world, it can be intimated to get started, so what can YOU do?
Well there’s no time like the present. There are user communities abound. Listen, I live in a rural state where my favorite urban legend says that there are more cows than people. If I can find a local community, so can you! Find one (meetup can be an excellent starting point) and go, even if it’s not in your wheelhouse. Especially if it’s not in your wheelhouse! Go learn something new, meet some interesting people and hopefully have a good time!
Got something worthwhile to share? A blog is stupid easy to create these days. I wouldn’t be here if it wasn’t! Only a year or two, it was really hard to podcast or create video equipment, as the equipment required was cost prohibitive to most. As we kick off 2020, there’s no reason not to share it loud a proud! And if creating online content isn’t enough for you, there are always conference CFPs (calls for papers) that are looking for passionate people to share their successes.
All of these options strike fear into your heart, but you’d still like to help others? Online opportunities are abound as well. Helping someone solve a problem or answer a question in a forum, benefits not just you and poster, but future assistance seekers as well.
Whatever the avenue, just do it! If you’re still not convinced, I’d like to give Kyle the last word on why we vCommunity. “Now, why do I continue to be involved… over the years, I’ve found it extremely rewarding to share my experiences and knowledge, become a mentor, [and] … build up a number of friendships that exist still to this day.”
Thank you to my friends quoted here and to all my friends out and about in the communities for all that you do.
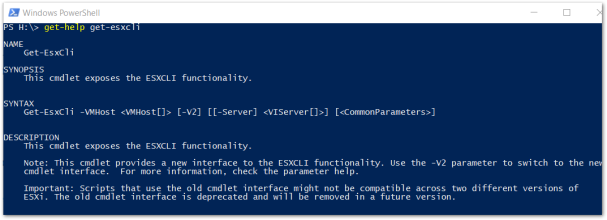
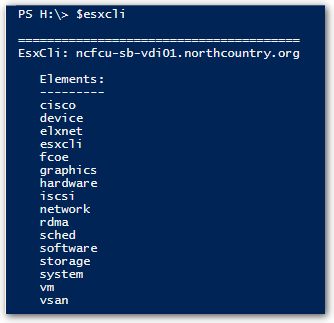



 However, with great power comes great responsibility. Because of the power presented with this tool, I’d recommend that you pay close attention to Role Based Access Control (among many other reasons). If you have a VM admin or operator with overly generous permissions, not only can they negatively impact your vSphere environment but they can also impact your VM’s as well, never mind compliance/auditing bag of worms that you can open.
However, with great power comes great responsibility. Because of the power presented with this tool, I’d recommend that you pay close attention to Role Based Access Control (among many other reasons). If you have a VM admin or operator with overly generous permissions, not only can they negatively impact your vSphere environment but they can also impact your VM’s as well, never mind compliance/auditing bag of worms that you can open.